Splunk’s Role in Strengthening Cybersecurity Across Modern Enterprises

In today’s digital-first world, cybersecurity threats are more dynamic and dangerous than ever. Enterprises face constant pressure to protect sensitive data, maintain compliance, and respond swiftly to incidents. Real-time security monitoring has become a critical pillar of modern defense strategies and Splunk Course in Bangalore is leading the charge.
The Shift Toward Real-Time Security
Gone are the days when periodic scans and manual log reviews were enough. Cyberattacks now unfold in seconds, and delays in detection can lead to devastating consequences. Real-time monitoring enables security teams to identify threats as they emerge, respond immediately, and minimize impact. But monitoring vast volumes of machine data from cloud platforms and endpoints to network devices and applications requires more than just speed. It demands intelligence, automation, and scalability. That’s where Splunk excels.
Splunk’s Role in Modern Security Operations
Splunk is a data analytics powerhouse designed to handle the complexity of enterprise environments. Its security capabilities are built around four key strengths:
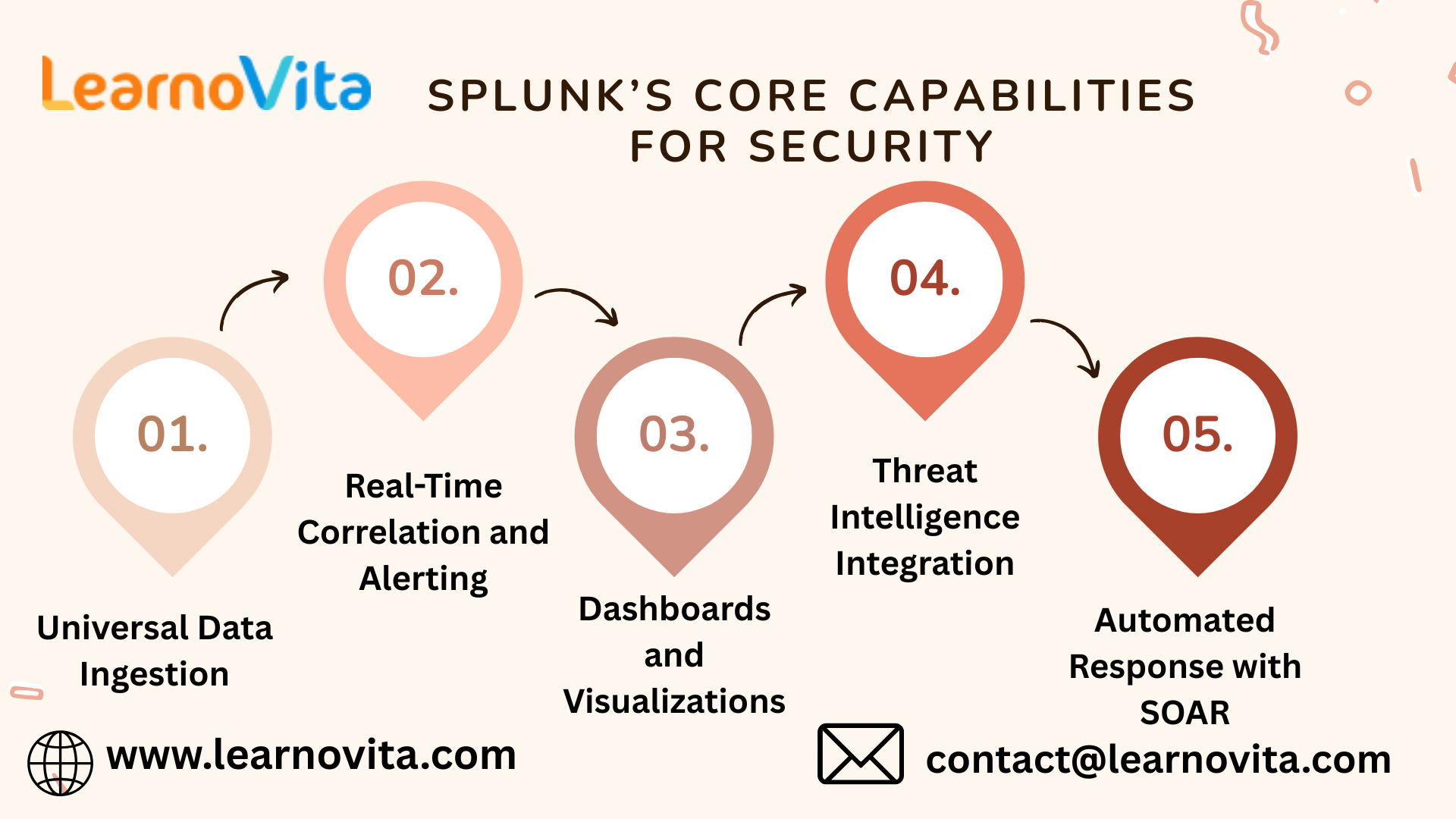
- Comprehensive Data Collection: Splunk ingests data from virtually any source, offering full visibility across on-premises, cloud, and hybrid infrastructures.
- Real-Time Detection and Alerting: With Splunk’s Search Processing Language (SPL), teams can define custom rules to detect suspicious behavior and trigger alerts instantly.
- Interactive Dashboards: Splunk’s intuitive dashboards provide live insights into threat activity, system health, and compliance metrics making it easier to prioritize and act.
- Security Automation with SOAR: Splunk’s Security Orchestration, Automation, and Response (SOAR) capabilities streamline incident response by automating repetitive tasks and orchestrating workflows across tools.
Use Cases That Matter
Splunk’s flexibility makes it a valuable asset across a wide range of security scenarios:
- Insider Threat Detection: By analyzing user behavior and access patterns, Splunk Online Course helps identify anomalies that may signal internal misuse.
- Regulatory Compliance: Splunk simplifies compliance reporting for standards like GDPR, HIPAA, and PCI-DSS by maintaining detailed audit trails and access logs.
- Cloud Security Monitoring: With native integrations for AWS, Azure, and Google Cloud, Splunk provides visibility into cloud workloads, configurations, and access controls.
- Endpoint Visibility: Splunk works seamlessly with endpoint detection tools to monitor malware infections, lateral movement, and unauthorized activity.
Why Enterprises Trust Splunk
Splunk’s real-time capabilities, scalability, and ease of use make it a trusted solution for security teams worldwide. Whether managing a small SOC or a global infrastructure, Splunk adapts to the organization’s needs. Its machine learning features further enhance threat detection by identifying patterns and predicting potential risks. By turning raw data into actionable intelligence, Splunk empowers teams to move from reactive defense to proactive protection.
Final Thoughts
In an age where cyber threats are relentless, real-time security monitoring is no longer optional it’s essential. Splunk provides the tools, automation, and intelligence that modern enterprises need to stay ahead of attackers. With Splunk, security teams gain the clarity, speed, and confidence to protect what matters most.
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Jeux
- Gardening
- Health
- Domicile
- Literature
- Music
- Networking
- Autre
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness



