Fortifying Cybersecurity in Manufacturing: A 5-Step Action Plan
As the manufacturing sector adapts to digital advancements, it encounters a range of cybersecurity risks. Safeguarding sensitive information and ensuring smooth operations are crucial. Here’s a practical five-step action plan to help manufacturing firms enhance their cybersecurity strategies.
For those looking to enhance their skills, Cyber Security Training in Bangalore programs offer comprehensive education and job placement assistance, making it easier to master this tool and advance your career.

1. Perform Routine Risk Assessments
Begin by identifying potential vulnerabilities in your systems. Routine risk assessments help you understand the specific threats your organization may face, whether from outdated software, unsecured devices, or human error.
- Action Steps:
- Schedule assessments quarterly.
- Involve representatives from various departments for a comprehensive review.
- Document findings and prioritize risks accordingly.
2. Establish Strong Access Control Protocols
Effective management of access to sensitive information is essential. Robust access control protocols ensure that only authorized personnel can access critical systems and data.
- Action Steps:
- Implement role-based access control (RBAC) to limit permissions.
- Regularly review and update access rights as necessary.
- Require multi-factor authentication (MFA) for sensitive accounts.
3. Keep Software and Systems Updated
Outdated software presents significant risks as a target for cyber attackers. Regular updates not only improve functionality but also close security gaps.
- Action Steps:
- Create a routine for checking and applying software updates.
- Utilize automated tools to facilitate the update process.
- Ensure all devices, including IoT devices, are included in the update strategy.
With the aid of Cyber Security Course in Online programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.
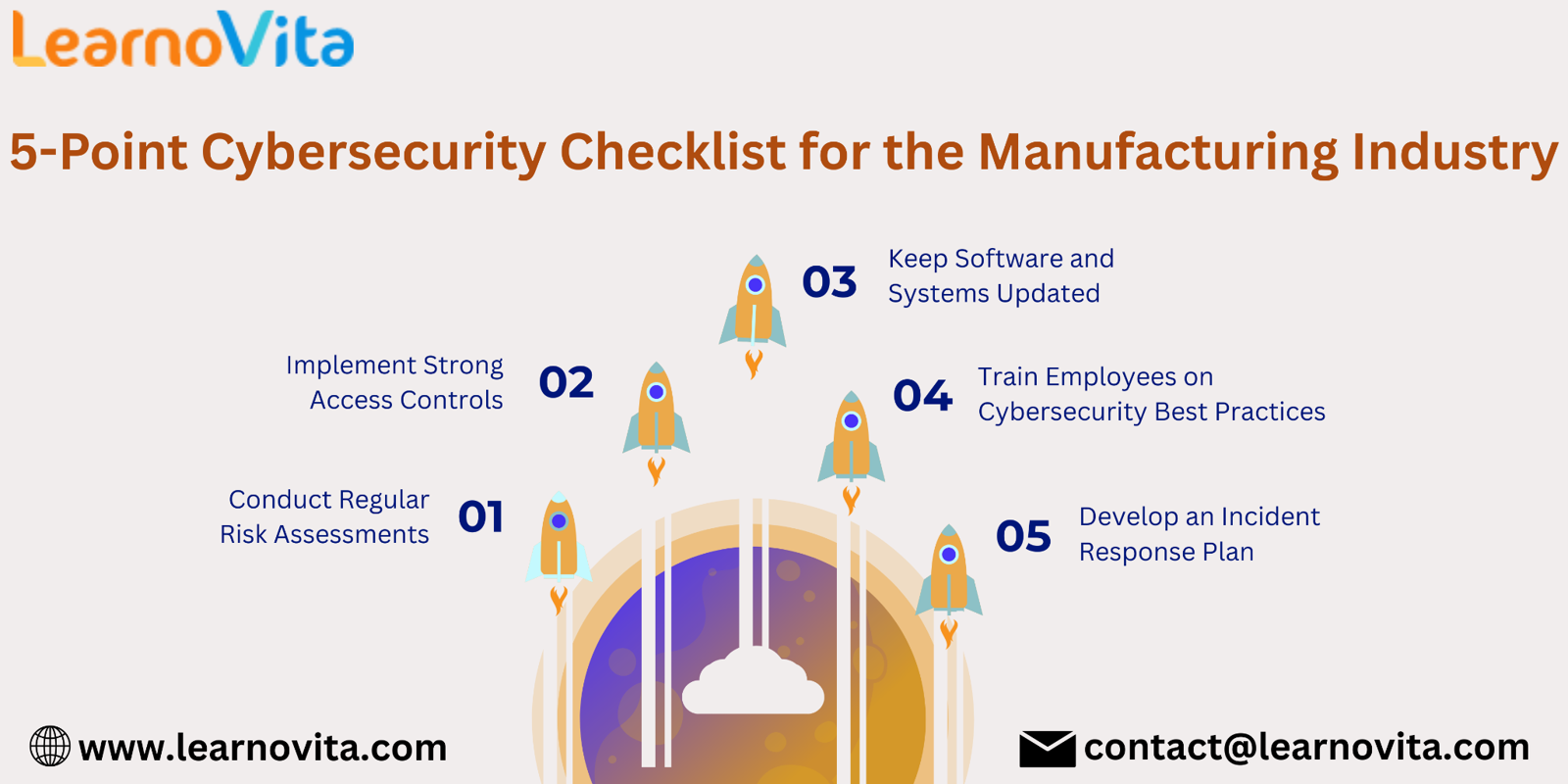
4. Educate Employees on Cybersecurity Practices
Employees serve as the first line of defense against cyber threats. Regular training helps them recognize phishing attempts, social engineering, and other common risks.
- Action Steps:
- Conduct monthly training sessions focused on cybersecurity awareness.
- Share updates on the latest cyber threats.
- Foster a culture of security mindfulness within the organization.
5. Develop a Robust Incident Response Plan
No system is completely immune to cyber threats. A well-defined incident response plan ensures that your organization can quickly address and recover from cyber incidents.
- Action Steps:
- Create a comprehensive response plan detailing roles and responsibilities.
- Conduct regular drills to test the plan’s effectiveness.
- Review and update the plan annually or after significant incidents.
Conclusion
Cybersecurity is an ongoing endeavor that requires dedication and proactive strategies. By following this five-step action plan, manufacturing companies can significantly bolster their security posture, protect sensitive information, and ensure operational continuity. Always remember, investing in prevention is far more effective than dealing with the fallout of a security breach.
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Juegos
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Other
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness



