How Penetration Testing Fits into a Comprehensive Security Strategy

Cybra delivers expert Penetration Testing services across Australia. Specialising in Penetration Testing Melbourne for networks and applications, Penetration Testing Brisbane with certified local teams, and Penetration Testing Sydney using cutting-edge tools and standards.
In today’s digital landscape, the importance of cybersecurity cannot be overstated. As businesses in Melbourne increasingly rely on technology and the internet to operate, they become more vulnerable to cyber threats. One effective way to evaluate and strengthen a company’s security posture is through penetration testing. This process not only identifies vulnerabilities but also provides actionable insights to mitigate risks.
Understanding Penetration Testing
Penetration testing, often referred to as "pen testing," is a simulated cyber attack on a system, network, or application to identify security weaknesses. The process mimics the strategies and techniques used by malicious hackers, allowing organizations to see their defenses from an attacker’s perspective. This proactive approach is essential for businesses aiming to protect sensitive data and maintain customer trust.
Types of Penetration Testing
-
Network Penetration Testing: This involves testing the security of network infrastructure. It assesses the risks associated with firewalls, routers, and switches to ensure they are properly configured and secure.
-
Web Application Testing: With the rise of online services, web applications have become prime targets for cybercriminals. This testing focuses on identifying vulnerabilities in applications, such as SQL injection and cross-site scripting (XSS).
-
Mobile Application Testing: As mobile usage continues to grow, so does the necessity for securing mobile applications. This type of pen testing evaluates security flaws specific to mobile platforms.
-
Social Engineering Testing: This aspect tests the human element of security, assessing how susceptible employees are to manipulative tactics that could lead to data breaches.
The Penetration Testing Process
The pen testing process typically involves several key stages:
-
Planning and Scoping: Defining the objectives, scope, and rules of engagement for the test. This stage ensures that all parties are aligned on what will be tested and how.
-
Reconnaissance: Gathering information about the target system. This can include identifying IP addresses, domain names, and potential points of entry.
-
Exploitation: Actively attempting to exploit identified vulnerabilities. This is where the tester simulates real-world attack scenarios.
-
Post-Exploitation: Analyzing the extent of the breach and the data that could be compromised. This stage helps in understanding the potential impact of an actual attack.
-
Reporting: Providing a detailed report that outlines findings, exploited vulnerabilities, and recommendations for remediation.
Benefits of Penetration Testing
-
Risk Assessment: By identifying vulnerabilities, businesses can prioritize their security efforts based on the level of risk associated with each weakness.
-
Regulatory Compliance: Many industries have compliance requirements regarding data protection. Regular pen testing can help organizations meet these standards.
-
Improved Security Awareness: Engaging in penetration testing fosters a culture of security within the organization, encouraging employees to adopt best practices.
-
Enhanced Customer Trust: When customers know that a business takes security seriously, it enhances their confidence in the brand, leading to stronger customer relationships.
Choosing a Penetration Testing Service in Melbourne
When selecting a penetration testing provider in Melbourne, it’s essential to look for accredited firms with a proven track record. Consider their experience in your industry, the methodologies they employ, and their ability to provide comprehensive reporting. Additionally, ensure they adhere to ethical standards and best practices in cybersecurity.
Conclusion
As cyber threats continue to evolve, penetration testing remains a critical component of a robust cybersecurity strategy for businesses in Melbourne. By proactively identifying and addressing vulnerabilities, organizations can protect their digital assets, comply with regulations, and maintain customer trust. In an era where data breaches can have devastating consequences, investing in penetration testing is not just wise; it is essential for survival.
Categorie
Leggi tutto
Relocating a distribution center isn’t just about moving boxes. It affects staff, equipment, systems, vendors, and deadlines. A poor move plan can trigger missed shipments, confused workers, and lost orders. If your move partner lacks the right approach, what should be a fresh start turns into a disaster. To avoid that, you need someone who plans each step with precision. A partner...

Hard rock music, with its signature heavy sound, fast tempos, and powerful guitar riffs, has become a staple in rock music history. But where did this genre come from, and who can be credited with its creation? To understand the roots of hard rock, we need to explore the evolution of rock music and how certain bands and musicians pushed boundaries. Hard rock is the product of several musical...

Need flyers or leaflets turned around quickly — without compromising quality? Our Flyer and Leaflets Printing London service is tailored for businesses, events, and campaigns that require speed, precision, and professional print standards. Whether you’re distributing promotional material or communicating key information, East London Printer is ready to deliver. Flyers and leaflets...

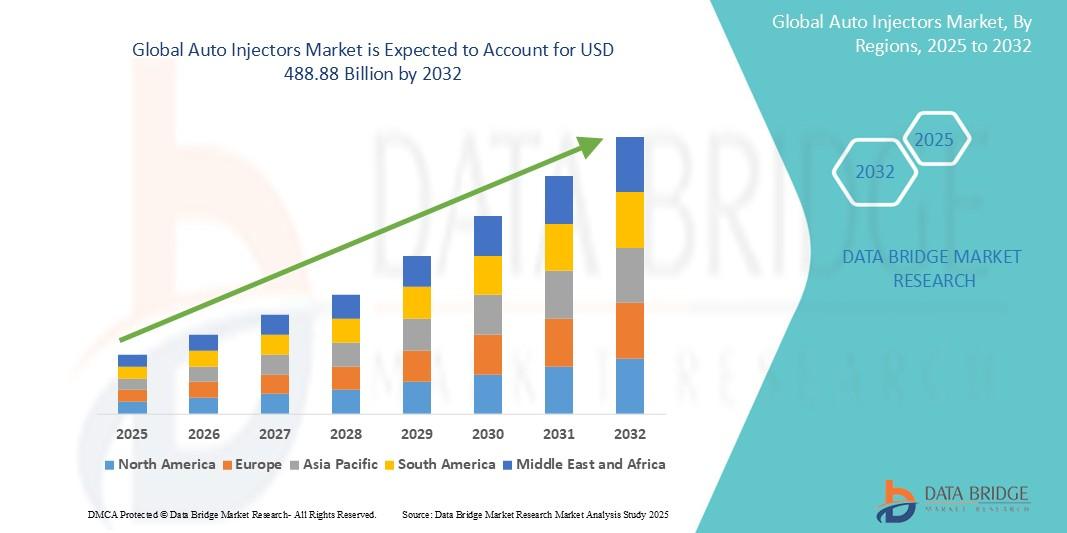
"Executive Summary Auto Injectors Market : The global auto injectors market size was valued at USD 101.13 billion in 2024 and is expected to reach USD 488.88 billion by 2032, at a CAGR of 21.77% during the forecast period The market study of Auto Injectors Market report helps minimize the risks of uncertainties and helps in taking sound...
When it comes to enhancing your home or commercial space, nothing adds elegance and durability quite like laminate flooring or wooden flooring. As one of the most trusted names in the global flooring industry, Kronotex delivers superior-quality flooring solutions that blend European craftsmanship with modern design—perfect for the dynamic needs of Indian interiors. Why Choose Kronotex...



