A Thorough Examination of Cybersecurity Risks
In an age where our lives are increasingly intertwined with technology, cybersecurity risks pose significant challenges to individuals and organizations alike. Understanding these risks is crucial for protecting sensitive information and maintaining the integrity of digital systems. This blog provides a thorough examination of the various cybersecurity risks we face today and offers insights into how to mitigate them.
If you want to excel in this career path, then it is recommended that you upgrade your skills and knowledge regularly with the latest Cyber Security Online Training.

What Are Cybersecurity Risks?
Cybersecurity risks refer to the potential threats that can compromise the confidentiality, integrity, or availability of digital information and systems. These risks can arise from various sources, including cybercriminals, insider threats, and even natural disasters. By understanding these risks, we can develop effective strategies to safeguard our digital assets.
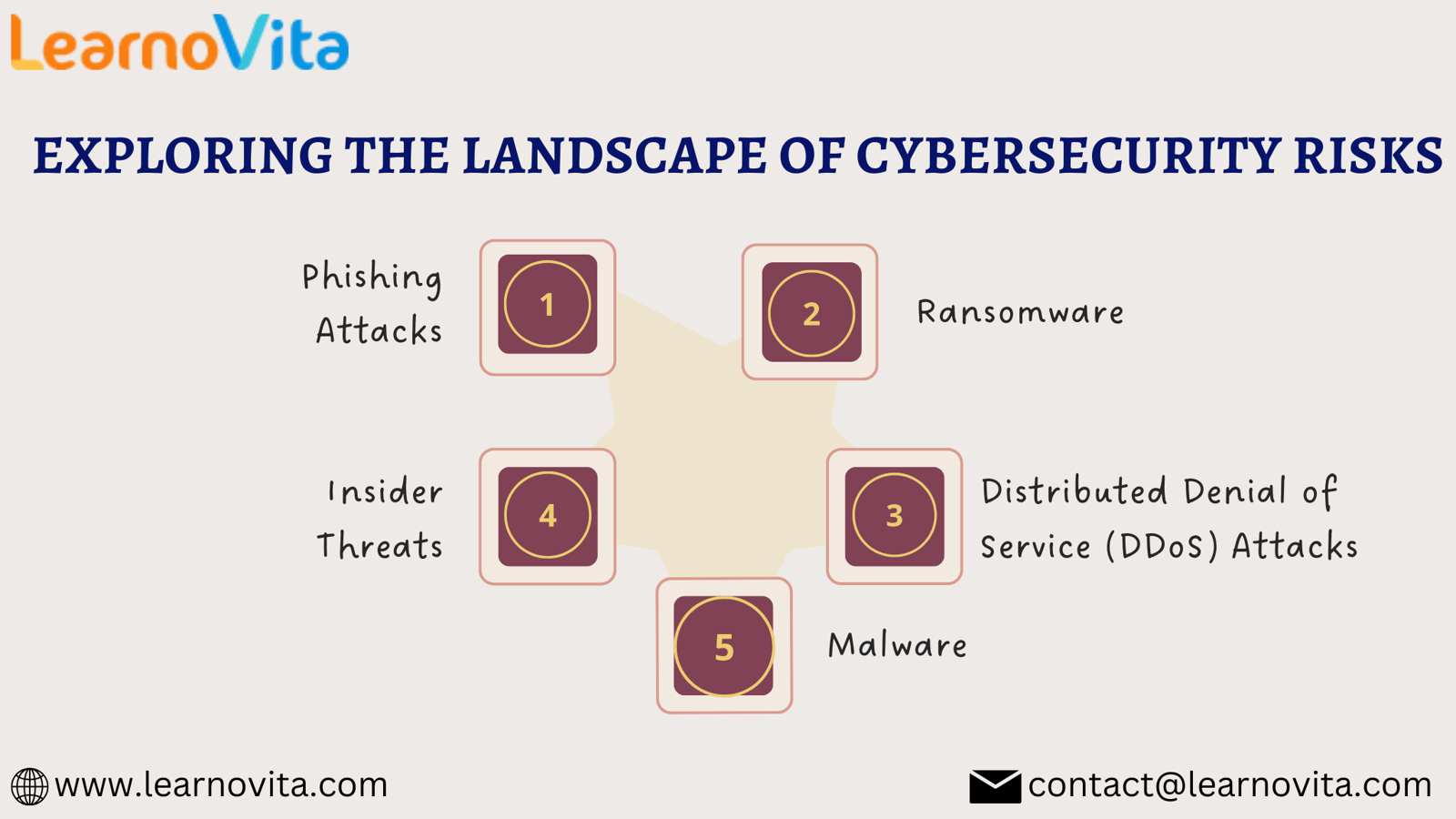
Key Cybersecurity Risks
1. Phishing Attacks
Phishing attacks are one of the most prevalent forms of cybersecurity risks. Cybercriminals send fraudulent emails or messages that appear to be from legitimate sources, tricking recipients into revealing sensitive information, such as passwords or financial details.
Mitigation Strategies:
- Always verify the sender’s email address.
- Be cautious of unexpected requests for personal information.
- Use advanced email filtering solutions to detect and block phishing attempts.
2. Ransomware
Ransomware is a particularly damaging type of malware that encrypts files on a victim's system, rendering them inaccessible until a ransom is paid. These attacks can cripple businesses, leading to operational disruptions and significant financial losses.
Mitigation Strategies:
- Regularly back up data and store it offline.
- Keep software and operating systems updated to patch vulnerabilities.
- Educate employees about the risks of ransomware and safe online practices.
3. Malware
Malware encompasses a wide range of malicious software designed to infiltrate and damage systems. This category includes viruses, worms, trojans, and spyware, each with unique methods of attack.
Mitigation Strategies:
- Install reputable antivirus and anti-malware software.
- Avoid downloading files from untrusted sources or clicking on suspicious links.
- Keep all software updated to close security gaps.
With the aid of Best Software Training Institute programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.
4. Insider Threats
Insider threats come from individuals within an organization who may compromise security, whether intentionally or unintentionally. This can include employees leaking sensitive information or neglecting security protocols.
Mitigation Strategies:
- Implement strict access controls and monitor user activity.
- Conduct regular training sessions on cybersecurity best practices.
- Foster a culture of transparency and security awareness within the organization.
5. Distributed Denial of Service (DDoS) Attacks
DDoS attacks flood a target’s systems with excessive traffic, overwhelming them and making services unavailable to legitimate users. These attacks can severely disrupt business operations and lead to significant downtime.
Mitigation Strategies:
- Use traffic monitoring tools to identify unusual spikes in activity.
- Invest in DDoS mitigation services to absorb and filter malicious traffic.
- Develop an incident response plan to address potential DDoS attacks quickly.
Conclusion
Cybersecurity risks are a complex and dynamic challenge in today’s digital landscape. By thoroughly examining these risks and implementing effective mitigation strategies, individuals and organizations can better protect their sensitive information and digital assets. Regular training, vigilance, and a proactive security posture are essential for navigating the intricacies of cybersecurity. Staying informed and prepared is the best defense against the ever-evolving threats in our interconnected world.
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- الألعاب
- Gardening
- Health
- الرئيسية
- Literature
- Music
- Networking
- أخرى
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness



