Empowering Identity Security: How CyberArk Strengthens Access Management in the Digital Era
In a time when digital transformation defines how businesses operate, the need to secure digital identities has become more urgent than ever. Every user, application, and system within an organization interacts with sensitive information that must be protected from unauthorized access. As enterprises expand across cloud, mobile, and hybrid environments, the boundaries of traditional security models have blurred. This shift has made Identity and Access Management (IAM) the foundation of cybersecurity strategy. Within this domain, CyberArk has emerged as a trusted leader, offering specialized solutions to protect privileged accounts, secure credentials, and prevent identity-based attacks. By focusing on the most powerful accounts within an IT ecosystem, CyberArk helps enterprises maintain trust, compliance, and resilience in an increasingly hostile cyber landscape. Enhance your cybersecurity skills with our CyberArk Course in Chennai, designed to equip you with hands-on expertise in privileged access management and identity security for modern enterprise environments.

Understanding the Significance of IAM
Identity and Access Management plays a crucial role in defining how digital identities are created, authenticated, and authorized across enterprise systems. As organizations move toward cloud computing and remote operations, the traditional perimeter-based security model has become obsolete. IAM ensures that access is granted only to verified users and strictly according to their assigned roles. However, while most IAM systems focus on standard user identities, privileged accounts, those that grant administrative or root-level control, require deeper protection. This is where CyberArk enhances traditional IAM strategies by introducing advanced privileged access controls, enabling organizations to safeguard critical systems from insider threats and external exploitation.
How CyberArk Elevates Privileged Access Management
Privileged accounts are often the primary target for cybercriminals because they hold unrestricted access to vital infrastructure and data. CyberArk provides a dedicated solution for securing and managing these privileged identities. It enforces least privilege principles, ensuring users only have access necessary to perform their tasks. By isolating privileged sessions and automatically rotating credentials, CyberArk reduces the likelihood of password misuse and unauthorized entry. It also maintains complete visibility into privileged activities, recording every session for future auditing. This unified approach strengthens the enterprise security framework, closing gaps that attackers often exploit through stolen credentials or insider access.
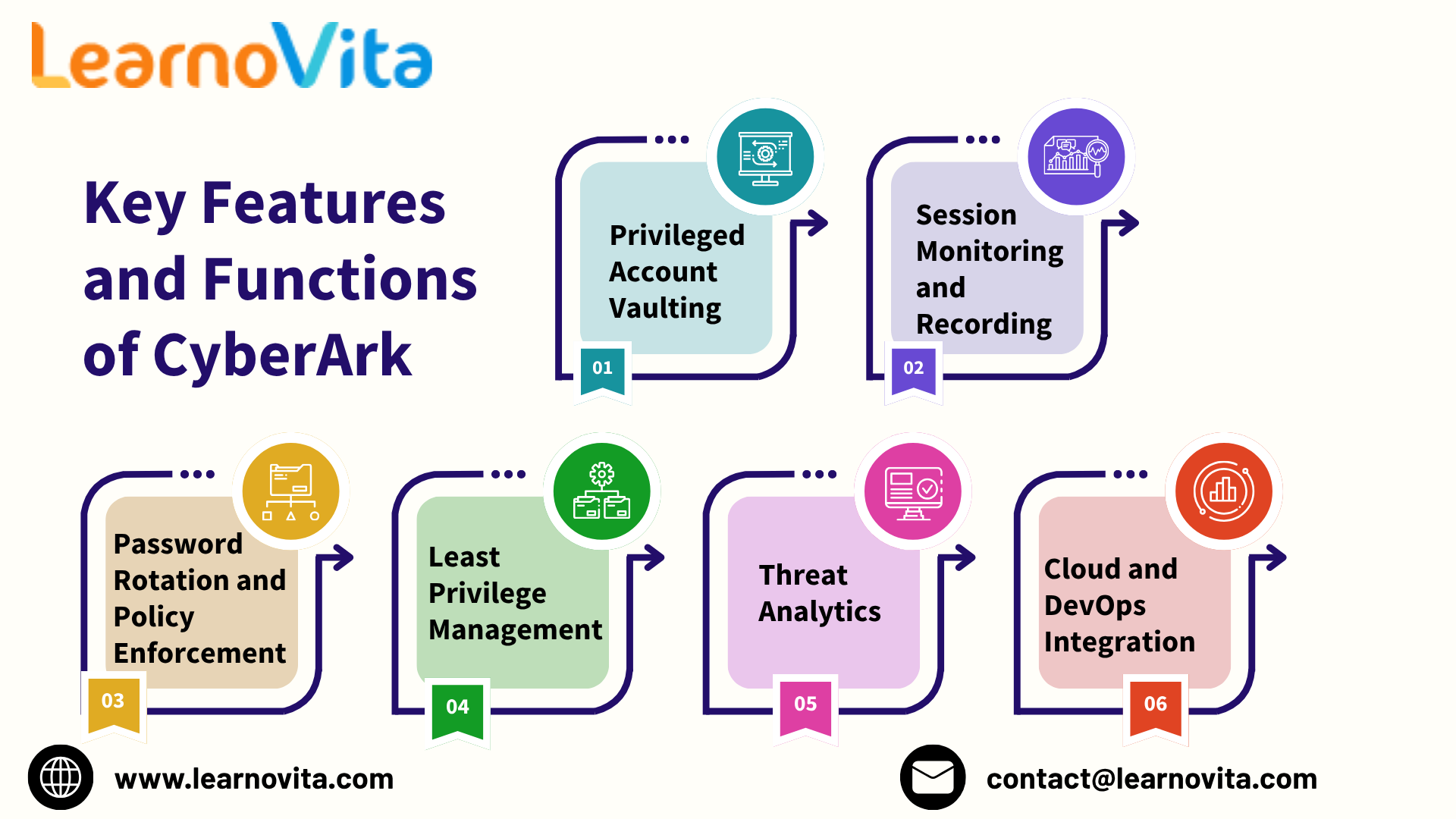
Key Features That Define CyberArk’s Excellence
CyberArk offers a comprehensive suite of tools designed to enhance access security and minimize identity-related risks. Its core features include:
-
Secure Password Vault: Safely stores privileged credentials in an encrypted vault to eliminate the risk of exposure or hardcoded passwords.
-
Automated Password Rotation: Regularly updates passwords to prevent unauthorized reuse and maintain password hygiene.
-
Session Isolation and Recording: Monitors privileged activities in real time and records sessions for detailed visibility and audit readiness.
-
Granular Access Control: Implements least privilege policies to limit user access based on need and role.
-
Behavioral Analytics: Detects unusual patterns and alerts administrators to potential threats or policy violations.
-
Cloud and DevOps Integration: Extends security to cloud platforms, APIs, and automation pipelines for full ecosystem protection.
Through these features, CyberArk provides complete control over privileged accounts, ensuring continuous protection across hybrid, on-premises, and cloud environments.
Ensuring Compliance and Strengthening Governance
For businesses operating under strict regulatory standards, maintaining compliance can be complex and time-consuming. CyberArk simplifies compliance efforts by automating credential management, access reporting, and session tracking. It helps organizations meet the requirements of standards such as GDPR, HIPAA, SOX, and ISO 27001, which demand clear visibility into privileged access. CyberArk’s built-in audit capabilities create detailed, tamper-proof logs that track who accessed sensitive systems, when, and for what purpose. This transparency allows security teams to identify potential policy breaches early and ensures that organizations remain audit-ready at all times. In essence, CyberArk not only reinforces compliance but also builds a culture of accountability within the enterprise. Advance your career in cybersecurity with our CyberArk Online Training, offering expert-led sessions that help you master privileged access management and secure digital identities from anywhere.
Aligning CyberArk with the Zero Trust Model
The Zero Trust security framework has reshaped the way organizations think about network protection. Based on the principle of “never trust, always verify,” this model requires continuous validation of every identity and access request. CyberArk seamlessly aligns with this approach by enforcing strong authentication, session monitoring, and just-in-time privileged access. It ensures that even internal users are treated as potential threats until verified. CyberArk also restricts lateral movement by isolating privileged sessions and validating actions in real time. This Zero Trust alignment makes CyberArk a vital component of any modern security architecture, helping enterprises minimize insider risks and ensure continuous identity assurance.
Business Advantages of Using CyberArk
Beyond improving technical security, CyberArk delivers measurable business benefits that impact efficiency, compliance, and operational stability. Some of the key advantages include:
-
Reduced Risk of Data Breaches: Protects high-privilege accounts, which are often the primary targets for attackers.
-
Operational Automation: Streamlines credential rotation, access approvals, and reporting to reduce administrative overhead.
-
Comprehensive Visibility: Offers a centralized dashboard for tracking privileged access and user activity in real time.
-
Improved Compliance Management: Simplifies audits through detailed access records and automated compliance reporting.
-
Cost Efficiency: Minimizes financial and reputational losses by preventing costly security incidents.
-
Enhanced Trust: Demonstrates strong governance and cybersecurity maturity to clients, regulators, and stakeholders.
These benefits prove that CyberArk is not only a cybersecurity solution, it’s a strategic investment in long-term operational resilience and trust.
Conclusion
In a threat landscape dominated by identity-based attacks, securing privileged access has become the cornerstone of enterprise cybersecurity. CyberArk plays a transformative role by combining advanced identity controls, automation, and analytics to protect sensitive systems from unauthorized access. Its alignment with IAM and Zero Trust principles enables organizations to maintain both agility and security across complex environments. By ensuring visibility, compliance, and accountability, CyberArk empowers businesses to build a secure digital future where trust is earned, not assumed. For any organization seeking to strengthen its cybersecurity foundation, CyberArk remains an essential ally in mastering identity and access management.
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Jocuri
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Alte
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness



