What is the Main Goal of Implementing DevSecOps in an Organization?
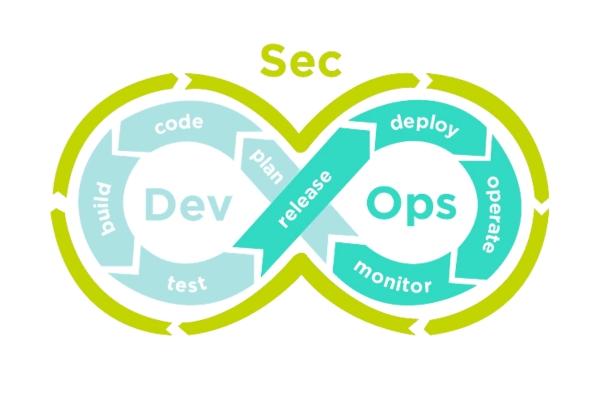
In today’s fast-changing digital world, cybersecurity has become a top priority for every organization. As businesses continue to adopt DevOps for faster delivery and innovation, security often becomes an afterthought leading to potential risks. That’s where DevSecOps comes into play.
DevSecOps combines development (Dev), security (Sec), and operations (Ops) into one integrated process. Its main goal is to make security an integral part of the software development lifecycle not an isolated or final step.
This blog explores the main goal of implementing DevSecOps in an organization, its benefits, real-world examples, and how professionals can upskill with DevSecOps training and certification to stay ahead in this evolving field.
1. The Evolution of DevOps to DevSecOps
From DevOps to DevSecOps: A Shift in Mindset
DevOps revolutionized software development by bridging the gap between development and operations teams. The focus was on faster delivery, automation, and collaboration. However, as speed increased, security often lagged behind.
DevSecOps evolved to solve this issue by embedding security practices within every stage of the DevOps pipeline. Instead of treating security as a separate layer, DevSecOps ensures that every developer, tester, and operations engineer is responsible for security.
In short:
DevSecOps = DevOps + Continuous Security.
This approach allows organizations to detect vulnerabilities early, reduce risks, and maintain compliance without slowing down development.
2. The Main Goal of Implementing DevSecOps
The main goal of DevSecOps is to integrate security as a shared responsibility throughout the software development lifecycle. Instead of relying on post-production security checks, DevSecOps ensures that security is embedded in every phase from planning and coding to deployment and monitoring.
Let’s break down this goal into specific objectives:
a) Security by Design
DevSecOps encourages teams to build security directly into the design of the application. Threat modeling, code reviews, and automated vulnerability scans help identify and address risks early.
b) Shift-Left Security
“Shift-left” means moving security testing earlier in the development process. By detecting vulnerabilities during coding and testing, organizations save time and avoid costly fixes later.
c) Continuous Security Integration
Automation tools ensure that security testing, scanning, and monitoring happen continuously throughout the CI/CD pipeline. This allows teams to maintain high velocity without compromising safety.
d) Shared Accountability
Every member of the DevOps team from developers to system administrators becomes responsible for security. This shared culture strengthens the organization’s overall defense posture.
e) Faster, Safer Delivery
DevSecOps ensures that security does not slow down innovation. With automated testing and compliance checks, teams can release secure software faster and more reliably.
3. Why DevSecOps Matters Today
The importance of DevSecOps cannot be overstated. According to IBM’s Cost of a Data Breach Report, the average cost of a data breach in 2024 was $4.45 million. Most of these breaches could have been prevented with early security integration.
Key Benefits of DevSecOps:
-
Early Vulnerability Detection:
Continuous scanning identifies risks before they reach production. -
Reduced Costs:
Fixing vulnerabilities early in the SDLC is significantly cheaper than post-deployment fixes. -
Improved Compliance:
DevSecOps automates compliance checks, helping organizations adhere to frameworks like GDPR, HIPAA, and ISO 27001. -
Faster Recovery:
Continuous monitoring and logging help teams detect, respond, and recover from incidents faster. -
Enhanced Customer Trust:
Secure applications strengthen brand reputation and build customer confidence.
4. Real-World Example: DevSecOps in Action
Let’s look at a practical scenario.
Example:
A financial organization adopted DevSecOps to secure its digital banking platform. Previously, its manual security audits took weeks, delaying releases. After implementing automated vulnerability scanning and container security checks in its CI/CD pipeline, the company reduced deployment time by 40% and detected 70% more vulnerabilities before release.
This success came from making security a daily routine instead of a quarterly task.
5. Core Components of a DevSecOps Strategy
A successful DevSecOps implementation relies on several core components:
a) Automation
Automation is the foundation of DevSecOps. Tools like Jenkins, GitLab CI, and automated testing frameworks streamline code scanning, configuration checks, and policy enforcement.
b) Continuous Integration and Continuous Deployment (CI/CD)
CI/CD pipelines integrate automated security tests to ensure every code change is validated before deployment.
c) Infrastructure as Code (IaC)
IaC tools like Terraform and Ansible enable secure and repeatable infrastructure provisioning, reducing human error.
d) Security Testing
Security testing includes:
-
Static Application Security Testing (SAST)
-
Dynamic Application Security Testing (DAST)
-
Dependency Scanning
-
Container Security Checks
e) Continuous Monitoring
Monitoring tools detect runtime threats, unauthorized access, and compliance violations in real-time.
f) Training and Awareness
Even the best tools fail if teams lack the right mindset. Continuous learning through DevSecOps training and certification programs helps professionals stay up to date with modern practices.
6. Step-by-Step Guide to Implement DevSecOps
Implementing DevSecOps can be challenging without a structured approach. Here’s a practical step-by-step guide:
Step 1: Assess the Current Environment
Start by evaluating your existing DevOps process. Identify where security is missing and define your security goals.
Step 2: Build a Security-First Culture
Promote awareness and accountability across teams. Every developer should understand the basics of secure coding and threat modeling.
Step 3: Automate Security Testing
Integrate automated security scanners into your CI/CD pipeline. For example:
-
SAST tools for code analysis
-
DAST tools for runtime testing
-
IaC scanners for misconfiguration detection
Step 4: Adopt Secure Coding Practices
Use secure frameworks, implement proper access control, and sanitize all inputs to prevent attacks like SQL injection and XSS.
Step 5: Monitor Continuously
Implement logging, intrusion detection, and compliance reporting tools. Regularly review security dashboards for anomalies.
Step 6: Train and Upskill Teams
Encourage team members to pursue DevSecOps training and certification programs from trusted institutes like H2K Infosys. These courses help professionals gain hands-on experience in securing CI/CD pipelines, cloud infrastructure, and containers.
7. How Cloud Platforms Support DevSecOps
DevSecOps thrives in cloud-native environments. Popular cloud providers offer integrated tools to automate security and compliance.
a) AWS and DevSecOps
With AWS DevSecOps certification, professionals learn to implement security automation using tools like AWS CodePipeline, AWS Inspector, and AWS Shield. These help in continuous vulnerability assessment and proactive defense.
b) Azure and DevSecOps
If you’re pursuing Azure DevOps training online, you’ll learn to embed security in build pipelines, automate compliance using Azure Policy, and use Defender for Cloud to identify threats.
c) Multi-Cloud Security
Modern organizations often operate in hybrid or multi-cloud setups. DevSecOps ensures consistent policies and monitoring across all environments.
8. DevSecOps and Automation Tools
Automation makes DevSecOps scalable and reliable. Below are commonly used categories of tools:
| Function | Example Tools |
|---|---|
| Code Analysis (SAST) | SonarQube, Checkmarx |
| Dynamic Testing (DAST) | OWASP ZAP, Burp Suite |
| Container Security | Aqua, Twistlock |
| CI/CD Pipelines | Jenkins, GitLab CI |
| IaC Scanning | Terraform, Checkov |
| Monitoring | Splunk, Prometheus |
By mastering these tools through structured programs like DevSecOps training and certification, professionals can manage complex DevSecOps pipelines efficiently.
9. Challenges in Implementing DevSecOps
Despite its benefits, DevSecOps comes with challenges:
-
Cultural Resistance:
Teams often resist change, especially when new security practices seem to slow development. -
Tool Overload:
Managing multiple security tools can become complex without proper integration. -
Skill Gaps:
Many professionals lack the skills to implement security automation effectively which makes DevSecOps training and certification vital. -
Compliance Complexity:
Meeting multiple compliance standards requires automated, auditable processes.
Solution:
Continuous education through H2K Infosys training helps teams overcome these barriers by teaching practical implementation methods using real-world case studies.
10. Measuring DevSecOps Success
Measuring the effectiveness of DevSecOps ensures continuous improvement. Key metrics include:
-
Mean Time to Detect (MTTD)
Measures how quickly vulnerabilities are identified. -
Mean Time to Remediate (MTTR)
Evaluates how fast teams fix security issues. -
Number of Security Incidents
Tracks improvement over time. -
Compliance Score
Indicates adherence to regulatory and internal policies.
Regular monitoring of these metrics helps organizations refine their DevSecOps pipelines.
11. How to Build a Career in DevSecOps
As organizations move toward cloud-native architectures, DevSecOps professionals are in high demand.
Skills Required:
-
Proficiency in DevOps tools and pipelines
-
Knowledge of cloud platforms (AWS, Azure, GCP)
-
Security testing and vulnerability management
-
Scripting (Python, Bash)
-
Familiarity with compliance frameworks
Learning Path:
Start with foundational DevOps knowledge, then pursue advanced learning through:
-
DevSecOps training and certification
-
AWS DevSecOps certification
-
Azure DevOps training online
-
DevOps and AWS training programs for cross-platform expertise
Institutions like H2K Infosys offer hands-on, project-based courses that prepare learners for real-world implementation. These programs help professionals design secure CI/CD pipelines, automate vulnerability testing, and manage cloud security efficiently.
12. Future of DevSecOps
The future of DevSecOps looks promising. With the rise of AI-driven security, zero-trust architecture, and cloud-native development, automation will become even more intelligent.
Organizations adopting DevSecOps today will be better prepared to handle emerging cyber threats tomorrow. Continuous training through the best DevSecOps certification programs will ensure professionals stay ahead of these changes.
13. Key Takeaways
-
Main Goal:
The primary goal of implementing DevSecOps is to make security a shared, continuous, and automated process throughout the software lifecycle. -
Benefits:
Faster delivery, reduced risk, improved compliance, and enhanced trust. -
Implementation:
Success requires culture change, automation, and ongoing training. -
Career Growth:
Professionals can boost their careers with DevSecOps training and certification, AWS DevSecOps certification, and Azure DevOps training online. -
Best Practice:
Continuous improvement, monitoring, and learning are essential to sustain DevSecOps success.
Conclusion
DevSecOps isn’t just a framework it’s a culture shift. It ensures that security is everyone’s responsibility, integrated into every phase of software delivery. Organizations that embrace this mindset achieve stronger security, faster innovation, and greater resilience.
If you want to build expertise in this field, start your journey with DevSecOps training and certification from H2K Infosys. Learn practical, industry-driven skills that prepare you for top roles in cloud security and DevOps automation.
Start learning today and secure your future with DevSecOps!
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Giochi
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Altre informazioni
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness



