The Critical Role of Identity Access Management: Enhancing Security with CyberArk
In an increasingly perilous cyber landscape, robust security measures have become essential. At the heart of these measures lies Identity Access Management (IAM). This blog post explores what IAM entails, its significance, and how CyberArk enhances organizational security.
If you want to excel in this career path, then it is recommended that you upgrade your skills and knowledge regularly with the latest CyberArk Online Training.

What Is Identity Access Management (IAM)?
Identity Access Management (IAM) involves the processes and technologies that organizations use to manage digital identities and control access to sensitive information. Its primary aim is to ensure that authorized users can access the right resources at the right times for valid purposes.
Key Components of IAM
-
User Identification: Establishing unique identifiers for all users within the organization.
-
Authentication: Validating user identities using methods such as passwords, biometrics, or multi-factor authentication.
-
Authorization: Regulating access based on user roles and permissions.
-
User Lifecycle Management: Overseeing user accounts from creation to deactivation.
-
Monitoring and Reporting: Tracking user activity and generating insights to detect potential security risks.
Why IAM Is Important
IAM is crucial for several reasons:
- Enhanced Security: By managing access to sensitive data, IAM helps prevent unauthorized access and data breaches.
- Regulatory Compliance: Many industries must adhere to stringent regulations that require effective IAM practices.
- Operational Efficiency: Streamlined IAM processes reduce the burden on IT teams and minimize human error.
- Improved User Experience: Features like Single Sign-On (SSO) enhance user satisfaction by simplifying access to multiple applications.
With the aid of Best Software Training Institute programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.
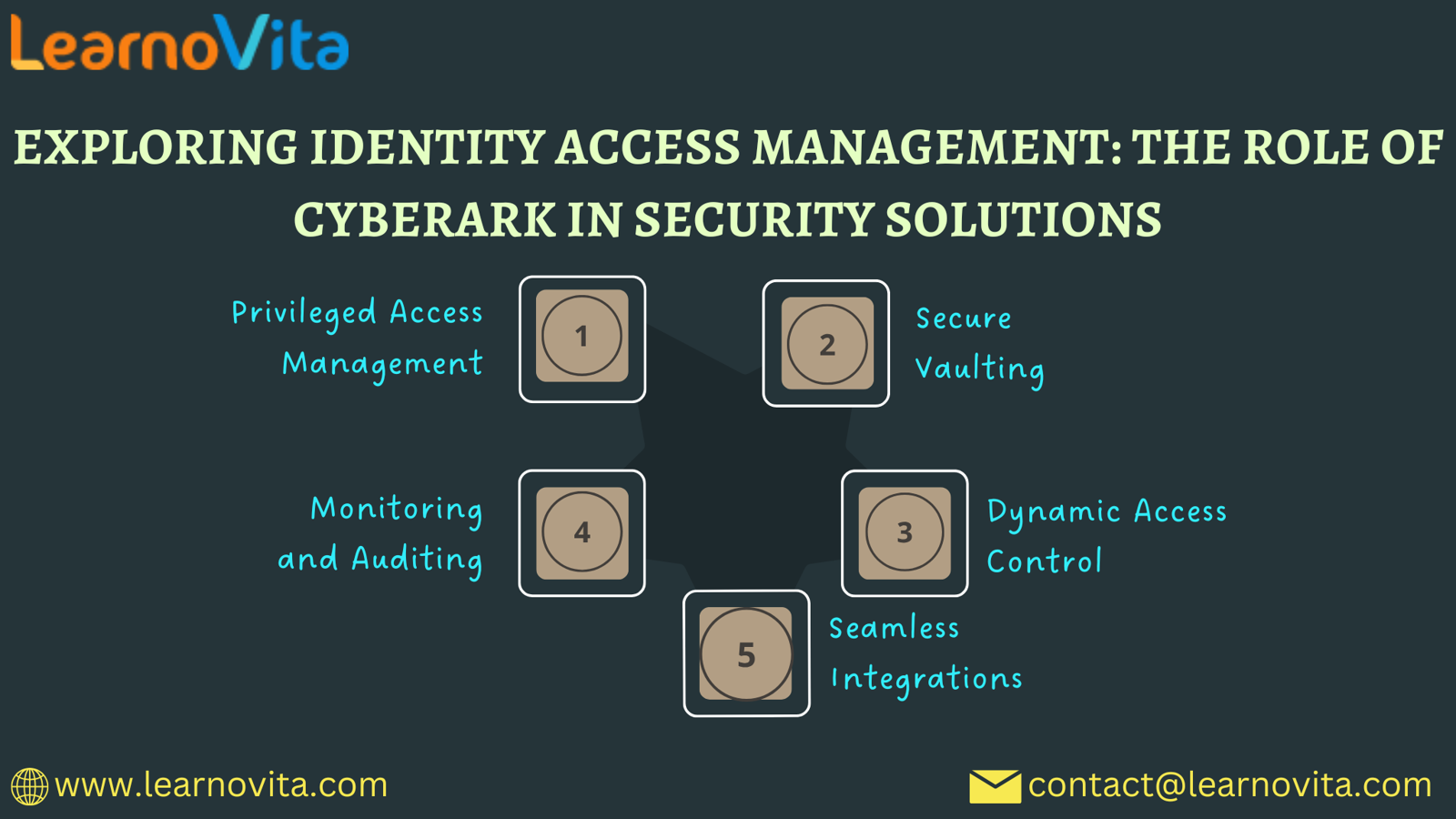
CyberArk’s Contribution to IAM
CyberArk is a leader in privileged access management (PAM) and plays a significant role in strengthening IAM frameworks. Here’s how CyberArk enhances IAM capabilities:
1. Securing Privileged Accounts
CyberArk specializes in managing privileged accounts that have elevated access rights, mitigating the risks associated with credential theft, a leading threat in cybersecurity.
2. Credential Vaulting
CyberArk provides a secure vault for sensitive credentials, ensuring that access is limited to authorized users. This approach protects against unauthorized credential usage.
3. Dynamic Access Control
CyberArk enables organizations to implement dynamic access controls that adjust based on user behavior and risk levels, allowing for quicker threat responses.
4. Comprehensive Monitoring
CyberArk offers extensive monitoring tools that track user activities and generate alerts for unusual behavior, enabling early detection of potential threats.
5. Easy Integration
CyberArk is designed to seamlessly integrate with existing IAM solutions, enhancing functionality without requiring a complete overhaul. This compatibility allows organizations to optimize their security investments.
Conclusion
Identity Access Management is a fundamental aspect of any organization’s security strategy. Given the increasing complexity of cyber threats, integrating effective solutions like CyberArk is essential for enhancing IAM practices. By effectively managing privileged accounts and access control, CyberArk helps maintain a robust security posture.
As organizations navigate the digital landscape, prioritizing IAM with powerful tools like CyberArk ensures that security remains a central focus. Protecting the critical asset of data requires a proactive approach, with IAM at the forefront.
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Spellen
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Other
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness



